Cyberwarfare & Cybersecurity of Critical Infrastructure- All You Need to Know

Industrial capacities and critical infrastructure are key targets in warfare. This has been so especially since the Industrial Revolution. Today, cyberwarfare poses a greater threat in this regard as it can cause much greater damage to the target with very little cost to the attacker. The ShadowPad attack on Mumbai’s electricity distribution grid has shown the damaging potential of cyberattacks directed at critical infrastructure. Though the energy sector is one of the most targeted in such attacks, it isn’t the only one. Sectors like transport, telecommunication, manufacturing units and other public sector services could be brought down by cyberattacks.
What was the ShadowPad attack on Indian powergrid?
- In October 2020, the power supply in Mumbai got cut off by a cyberattack. This power out was at an important period of the day- between 10 AM and 12 noon- when the stock market is active and commercial activities
- October was also the period when India saw peaking of COVID-19 cases and Mumbai was struggling with one of the highest caseloads in India.
- It resulted in the stock market shutting down, trains grinding to a halt, businesses affected by lack of power supply and the hospitals falling back on emergency power supply to perform its crucial functions.
- This was traced to a malware called ShadowPad and the attack was launched by a Chinese state backed hacker group called Red Echo, according to the US-based cybersecurity company, Recorded Futures.
- The report claimed that a large number of malwares were being transmitted from Chinese actors to Indian entities over a period of time in what is called a ‘prepositioning’ move. This means that a string of malwares are put in place across the target’s infrastructure network to be activated at a strategically timed moment to produce maximum damage.
- All this was done in the backdrop of the Galwan Valley clash between India and China followed by the high level talks for de-escalation.
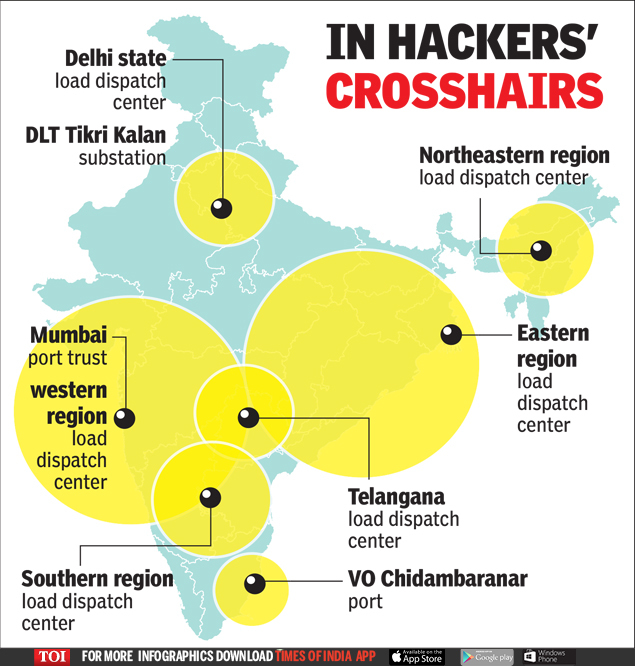
- Later reports identified that the attack had affected 12 critical infrastructure entities- 10 power sector organizations and 2 maritime sector organizations.
- The Recorded Future report said that this isn’t so much an act of aggression as of deterrence in context of the border tensions between India and China.
What is ShadowPad?
- ShadowPad is a trojan malware that was designed to target supply chain infrastructure in sectors like energy, telecommunication, transport, etc.
- It opens a secret route between the targeted system and the command and control servers through which the attackers can extract information or deliver more malicious codes.
- They are introduced into the target system primarily through trojanized softwares.
- The malware can steal sensitive information from the infected system and send it back to the hackers’ command servers, once every 8 hours. When the hackers find an ‘interesting target’, they can seek more information from the infected system or send in even more malicious code.
- The malware was first detected in 2017 as infections in software updates from NetSarang, a legitimate software provider. The attack was attributed to APT41, a cyber threat group that carries out espionage attacks for the Chinese state.
- APT41 is reported to have targeted organizations in 14 different countries since 2012, especially to steal intellectual property.
How is the Indian infrastructure being targeted?
- India has been facing an increasing number of cyberattack attempts with each passing year.
- But the attacks on it critical infrastructure hasn’t been many. However, the ShadowPad attack is not the first such cyberattack on Indian infrastructure.
- Most of such attempts have been directed against the power infrastructure, banking sector, manufacturing infrastructure and healthcare infrastructure.
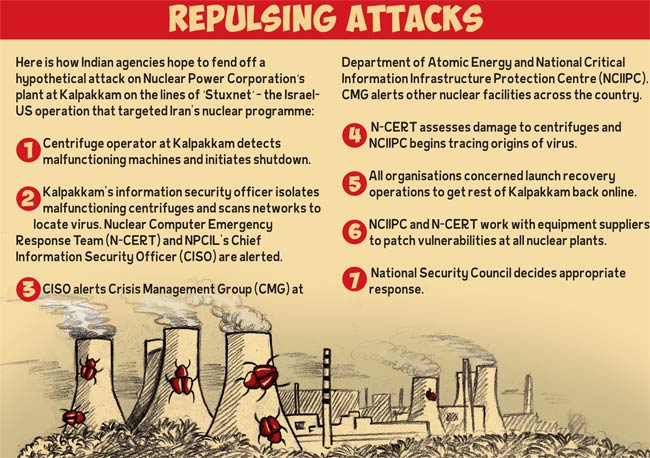
- In 2019, the Kudankulam Nuclear Power Plant in Tamil Nadu suffered an infection in its system used for administrative purposes. The malware ‘DTrack’ was determined to be behind the attack.
- Since the start of the pandemic, the number of cyberattacks on infrastructure has spiked.
- The number of COVID-related phishing campaigns targeting government, defense and critical infrastructure has increased in the recent times.
- Just a month after the attack on Mumbai’s infrastructure, CERT-In reported the ShadowPad malware in a number of supply chain attacks– one of the largest such attacks to be detected. Many of these emanated from a single IP address.
- Another Chinese hacker group, Stone Panda (According to Cyfirma, a cyber intelligence firm) targeted the supply chain softwares of Bharat Biotech and Serum Institute of India by identifying vulnerabilities in their IT infrastructure. These companies are currently involved in manufacturing COVID vaccines and have a critical role in India’s fight to control the virus. They are also involved in vaccine trials.
- Apart from Chinese hackers, hackers from Russia and North Korea are also targeting these two vaccine manufacturers. Several Indian companies involved in developing COVID vaccine reported a hundred fold increase in cyber-attack attempts.
- These attacks are targeting the Indian pharmaceutical infrastructure especially for gaining access to the clinical trial information. India is conducting vaccine trials not only for the indigenous vaccines but also for several vaccine candidates developed abroad.
- In addition to this, with the shift to the hybrid work model, the country’s IT infrastructure is experiencing an increased number of cyber-attacks in the form of ransomware, malware and phishing. Some companies saw a 100% increase in such attempts.
- APT 29, a Russian group, has been targeting AIIMS, India’s apex public hospital and also other hospitals across the world.
- APT 10, a Chinese group, has been targeting 17 global organizations including India’s Sun Pharma, Bharat Biotech and AIIMS.
- North Korean group has been targeting 14 organizations across the world. India’s Patanjali, SII and Reddy’s feature on the list.
What is happening elsewhere?
- In 2007, a wave of cyberattacks targeted Estonia’s parliament, government ministries, banks and even the media.
- In 2008, Georgia’s telecommunication system was attacked when it was at war with Russia.
- In 2015, the Ukrainian power grid faced a SCADA or supervisory control and data acquisition cyberattack from Russia. This was launched via spear phishing emails which enabled infection with BlackEnergy malware. This is the 1st known case of a power outage caused by cyberattack.
- In 2014, a SCADA attack forcibly shutdown a furnace in a German steel mill leading to major damage. Social engineering techniques were used to gain control of the blast furnace system.
- In 2015, the Polish national airline grounded its aircrafts after its flight plan system suffered a DDoS (distributed denial of service) attack.
- In 2015-16, the global bank messaging system, SWIFT, was compromised by cyber-attacks. Millions of dollars were stolen through this attack by Lazarus, a North Korean hacker group.
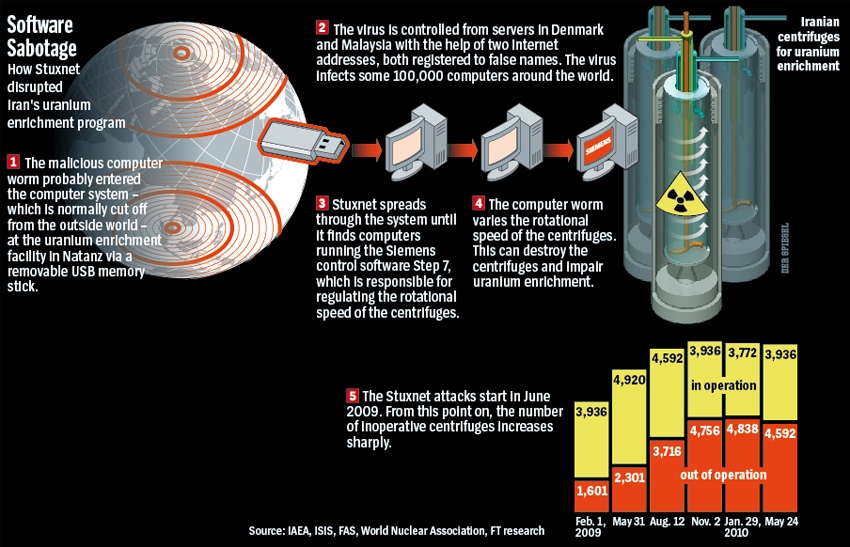
- One of the most significant example of use of cyberattacks to target critical infrastructure was the Stuxnet attack on Iran. The worm was jointly created by USA and Israel to target the Iranian nuclear program. It led to the destruction of more than a 1,000 nuclear centrifuges, causing a major setback for Tehran’s atomic program.
- After the Stuxnet worm, another malware Industroyer was discovered. This malware was designed specifically for taking over control of electricity sub-station circuit breakers. This means that it could not only damage the power stations but also the control systems of transportation, water supply and gas plants.
- USA and Russia have been targeting each other with various malwares. Power grids are one of the key targets.
- Even after the change of government in the USA, the Chinese are reported to have infected multiple government agencies and over a 100 corporations.
- Even dams have been attacked in the past. In 2013, USA’s Rye Brook Dam faced a cyberattack from Iranian hackers. The attack itself came to light only in 2016. This attack raised major concerns among security experts given its implications for larger dam projects.
- New Zealand recently suffered DoS cyberattacks on its stock exchange operator which prevented trading for days. Following this, even its Reserve Bank was attacked.
Why are countries resorting to such attacks?
- It has become increasingly difficult for countries to fight old fashioned physical wars. These involve many casualties irrespective of victory or defeat. A case in point is the loss of lives suffered by the USA in its wars in Iraq and Afghanistan.
- Such casualties don’t sit well with the public and they have deleterious political implications for the ruling government. Hence the governments have lost the appetite for physical warfare.
- Cyber warfare can serve the same purpose as conventional warfare but without incurring physical losses.
- In addition to this, cyber weapons are becoming cheaper and more readily available.
- It enables pre-positioning. malware assets can be placed in crucial spots in the target state’s infrastructure and can be activated whenever desired. Some states use this as a supplementary tactic during regular wars.
- Icing on the cake is it gives plausible deniability. The attacking state could easily shift the blame to someone else.
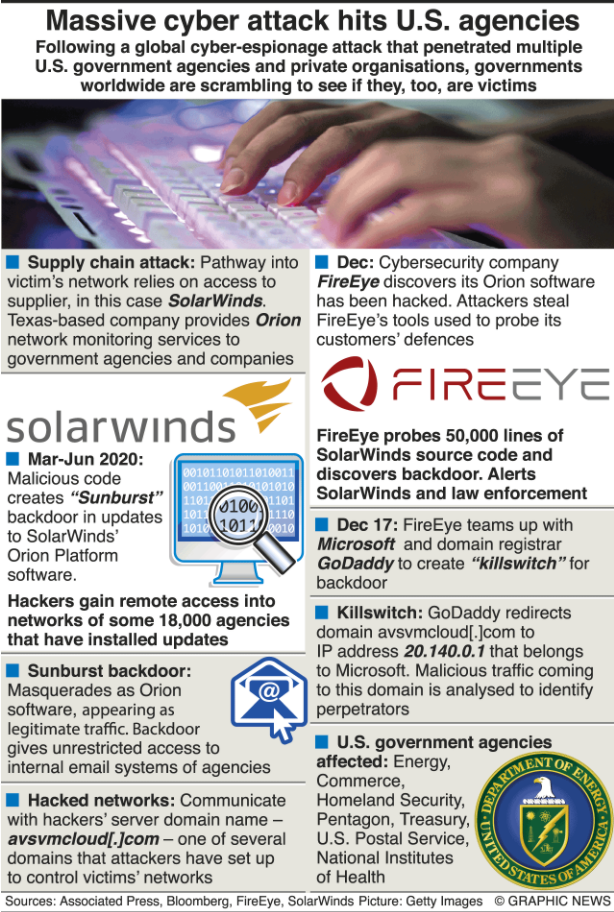
- Many of the cyberattacks is for stealing sensitive or valuable information. These can be used against the target state in international politics or thwart covert operations. In one of the biggest cyberattacks in recent times, the SolarWinds hack, multiple government agencies in the USA including the commerce, treasury and the homeland security departments were affected.
- The emergence of supply chain attacks has reduced the need for cybercriminals to directly target the government network. They could simply gain access to the target grid via niche softwares that are used by these networks. Eg: Sunburst malware was introduced into the US government’s computer network via the Orion software.
- Corporate espionage– some of these stolen data is used to gain a competitive edge with respect to production and exports. Eg: the recent surge in the number of attacks targeting pharmaceutical sector in USA, UK, Japan, Australia, South Korea, Germany, Taiwan, etc. Data like vaccines’ clinical trial information, logistics plan, distribution plan, etc. were of particular interest to these attackers.
- The theft of such information could also be used by the attacking countries to damage the target country’s reputation.
- Sometimes, these cyber-attacks on infrastructure are used to distract the target country from the actual attack elsewhere.
What has Indian done to secure its infrastructure against such attacks?
- CERT-In is India’s Computer Emergency Response Team under the Ministry of Electronics and IT. Its main role is to proactively secure India’s cyber space.
- Some of its functions include:
- Collection and analysis of information on cyber-incidents.
- Issuing guidelines, advisories and whitepapers for cyber-security.
- Forecasting and raising alerts of such incidents.
- Handling such incidents using emergency measures.
- Coordinating response against such incidents.
- CERT-In conducts regular training programs for network administrators to counter cyber-terrorism.
- It formulated the Cyber Crisis Management Plan for implementation by all departments, both at center and in the states, in critical sectors.
- With rise in threats faced by infrastructure, the NCIIPC (National Critical Information Infrastructure Protection Centre) was constituted in 2014. Since then, CERT-In has been concerned with computer security incidents while NCIIPC has been given the task of protecting India’s critical information infrastructure. These two bodies have been working closely with various government agencies.
- An exclusive cyber crisis management plan was formulated for the power sector. It gave the framework for identification of critical information infrastructure, incident response coordination and measures for mitigation. It envisages a layered approach to cyber security.
- It also called for periodic mock drills in power distribution utilities to make the operators aware of alternate methods to bring the system under control and to build cyber-resilience.
- To address the security needs of industrial automation and control systems, the BIS released the Industrial Cybersecurity Standards.
- In 2019, the National Mission on Interdisciplinary Cyber-Physical Systems (NM-ICPS) was announced with a budget of 3,660 crore INR for a period of 5 years. Cybersecurity of physical infrastructure is one of the focus areas.
- In the National Power Grid, the communication between substation equipment and the control centers is through POWERGRID-owned dedicated optical fiber network. These aren’t connected with the external networks and enjoy additional protection in the form of multiple firewalls.
- The National Cyber Security Strategy is being formulated by the National Cyber Security Coordinator.
What are the challenges and concerns?
Attractions of cyberwarfare:
- Unlike in case of a traditional cyberattack on a computer system, attack on cyber-physical systems can lead to actual destruction of assets like computer controlled generators. Replacing them costs money and time. This is even more expensive if the spare parts aren’t domestically manufactured or aren’t readily available.
- Launching a cyber-attack on critical infrastructure is becoming increasingly cheaper. Use of spear phishing e-mails to target infrastructure is one such low cost approach.
- They are also becoming readily available on the Dark Web. Eg: the tools used for the attack on Ukraine’s power grid are easily available on the Dark Net. These tools were previously stolen from USA’s NSA.
Issues in infrastructure establishments:
- Most of the critical infrastructure has been designed for productivity and reliability, but not much focus has been paid to the security aspect. Many of these installations use legacy softwares that aren’t updated often enough.
- These installations rely more on physically secured and isolated environments for security. Such isolations pose no impediment for cyber-attacks.
- While the IT system has evolved with the times, the security features of industrial control systems has remained underdeveloped. Operational technology is the weak link in cybersecurity of infrastructure.
- Industrial control system arena is not as well served as IT infrastructure with cybersecurity services, products, consultants, etc.
- Critical infrastructure is becoming more interconnected– geographically and across sectors. It is also becoming increasingly complex. This implies that an attack on one node of the network could give rise to a devastating domino effect on other connected nodes. The emergence of IoT technology would further increase this vulnerability.
- The rise of highly distributed IT infrastructure with numerous devices operating on an unsecured networks has turned the situation even more favorable for cyber-attacks. This distributed framework has become more prevalent with the adoption of hybrid work models by firms in light of the lockdown.
- The governments are expediting the digital transformation initiatives to ensure inclusion of the less developed sections of the society and to meet the increasing demand for services. The digitalization of critical infrastructure proportionally increased the threat from cybercriminals in the absence of adequate protection.
Issues in response:
- India often faces power cuts and sometimes even large scale power grid failures. There is a general tendency to ignore possible attacks on its power infrastructure and move on.
- Lack of quick response to expert warnings on vulnerabilities in the system. In the recent New Zealand’s Reserve Bank attack, the cybercriminals targeted a legacy software (used by the bank for transferring large files) to gain access into its systems. The bank had earlier received warning about this vulnerability but put off addressing it because it was ‘still functional’.
Shortcomings in policy and capacity:
- Cyber-security capacities in India mostly exist outside the government. Given India’s relatively low cyber-security maturity, India is viewed as an easy target.
- The information about cyber-incidents aren’t voluntarily made public. This lack of information puts other government bodies and firms at risk as they remain ignorant about their vulnerability.
- Lack of clarity with regards to the government chain of command in the cyber-security area.
- Serious implications on diplomatic efforts. Eg: the Red Echo attack came at a sensitive time for Indo-China ties. Such attacks could be perceived as firing a shot across the bow.
Strategy issues:
- The general cybersecurity strategy focuses on the cyber-attacks in the past to prepare for response to future attacks. While this prevents reoccurrences, it doesn’t address the threat from novel cyber-attacks. This is especially a cause of concern as the field is dynamic and rapidly evolving. Sometimes, cyber criminals take advantage of this tendency to make their attacks more effective and unpredictable.
- Multiple countries are ramping up their cyberwarfare capabilities.
- Complete protection from cyberattacks isn’t possible. Eg: the US infrastructure fell victim to the SolarWinds hack despite its high spending for cybersecurity.
What is the way ahead?
- India cannot afford to ‘go retro’ as USA did with its Securing Energy Infrastructure Act that sought to replace automated systems in the power grid with low tech alternatives. In contrast, India must fortify its cyber-security infrastructure with appropriate backup options.
- For Indian industry to be efficient and competitive, automated operational processes is vital. But this has to be secured. For this, BIS’ Industrial Cybersecurity Standards must be adopted as soon as possible.
- A strong regulatory framework for utility companies should be put in place to strengthen their operational technology network. This regulation can be along the line of USA’s NERC (Electric Reliability Critical Infrastructure Protection) Policy.
- Critical infrastructure enterprises must weave security into all its layers- at levels of software and hardware.
- AI technology can be used for real time threat detection and for protection of critical infrastructure. AI-based security tools can weed out even the hidden malwares. If used appropriately, this could help address the pre-positioning attempts of threat actors.
- More focus should be given to how a cyberattack can be mitigated rather than where it might originate from. This approach would help reduce damage.
- When it comes to formulating crisis management plans, visionary thinking is needed. The planners should factor in the cybersecurity trends and emerging cyber weapons.
- Going forward, CERT-In and NCIIPC have a larger role to play in ensuring national security. These bodies need to be fortified with human resource and functional capacity.
- Though increased spending on cybersecurity doesn’t always guarantee 100% protection, poor budgetary allocation is like putting the nation’s critical infrastructure out in the open for cybercriminals to attack and manipulate.
- There is a need to incentivize the identification and reporting of cyber risks and also the development of indigenous solutions for cybersecurity. Startups and white hat hackers could be encouraged through competitions and bug bounty programs. Even the US Pentagon has started using such programs.
- There is a talent deficit in the cybersecurity space. India needs to encourage more public- private interactions to improve its capabilities. Private firms and educational institutions are key areas from which such talent can be developed. A network of cyber-warriors can be put in place.
- Improving awareness and conducting periodic drills for the personnel can help prevent at least the low tech attacks. It will also give them a clear route of action in case of a larger attack and this will prevent large disruptions.
- As complete cyber-defence isn’t possible, deterrence is the next best option.
- Clarity on cyberwarfare doctrine and strategic goals is necessary for structured addressal of the problem.
Conclusion:
The ShadowPad attack has shown that today’s wars aren’t fought only on the borderlines and the whole world could become the battlefield through cyberwarfare. Malwares are taking their place alongside tanks and missiles as destructive weapons. How much capacity a country has in the cyberspace is a new determinant of national power. This along with the increasing digitalization and advent of disruptive technologies like IoT are set to create a perfect cybersecurity storm. India needs to step up its game to proactively manage cyber risks and strengthen its cybersecurity capabilities.
Practice question for mains
In light of the 2020 Mumbai blackout, assess the need for developing India’s cybersecurity capabilities in the critical infrastructure area. Should digitalization in critical infrastructure be reversed? (250 words)
https://www.youtube.com/watch?v=5_S7JxHwDdg&t=823s
https://www.youtube.com/watch?v=5_S7JxHwDdg&t=823s
https://www.thehindu.com/sci-tech/technology/red-echo-over-india/article34008299.ece
https://indianexpress.com/article/opinion/columns/mumbai-electric-grid-china-cyber-attack-7221534/
https://indianexpress.com/article/explained/explained-chinas-cyber-eye-and-india-7211655/
https://www.dnaindia.com/india/report-centre-prepares-cyber-crisis-management-plan-2567753
https://techmonitor.ai/techonology/cybersecurity/top-5-infrastructure-hacks
https://pib.gov.in/PressReleasePage.aspx?PRID=1594760
https://www.businesstoday.in/magazine/features/india-cyber-security-at-risk/story/191786.html
https://hbr.org/2020/01/how-to-safeguard-against-cyberattacks-on-utilities
http://www.newsonair.com/Main-News-Details.aspx?id=356599
https://www.deccanherald.com/specials/did-china-just-wake-us-up-to-cyberwar-959065.html
https://nciipc.gov.in/documents/NCIIPC_Newsletter_Jan21.pdf
If you like this post, please share your feedback in the comments section below so that we will upload more posts like this.