Akira Ransomware
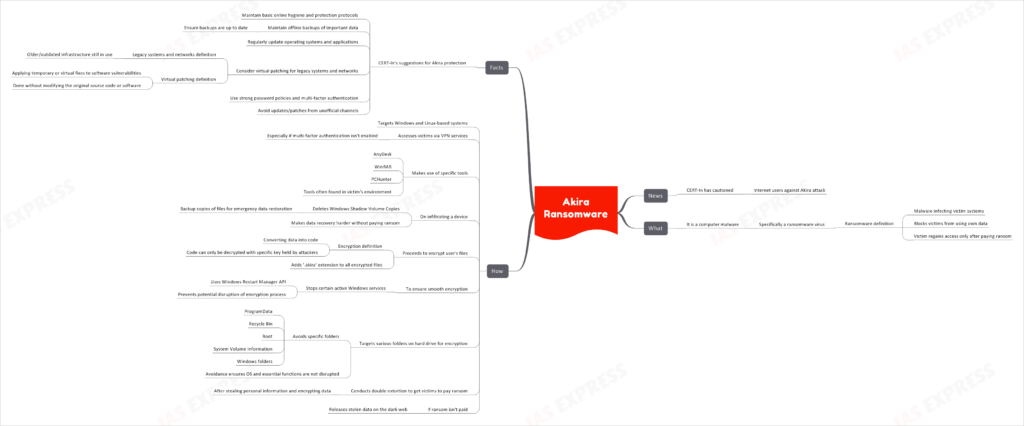
In recent news, CERT-In has issued a warning to internet users against Akira attacks.
What is Akira Ransomware?
- Akira is a computer malware, specifically a ransomware virus.
- Ransomware is a type of malware that infects victim systems and blocks the victims from using their own data.
- The victim can regain access only upon paying the ransom.
How does Akira Operate?
- Akira targets Windows and Linux-based systems.
- It accesses victims via VPN services, especially when multi-factor authentication isn’t enabled.
- It uses tools like AnyDesk, WinRAR, and PCHunter, which are often found in the victim’s environment.
Infiltration and Encryption
- Upon infiltrating a device, Akira deletes the Windows Shadow Volume Copies, which are backup copies of files used for emergency data restoration.
- After deleting the Shadow Volume Copies, it becomes harder for the user to recover their files without paying the ransom.
- It then proceeds to encrypt the user’s files by converting data into a code that can only be decrypted with a specific key, which is held by the attackers.
- During the encryption process, Akira adds a ‘.akira’ extension to the names of all encrypted files.
- To ensure a smooth encryption without interruptions, the ransomware stops certain active Windows services using the Windows Restart Manager API.
Targets and Extortion
- Akira targets various folders on the hard drive to encrypt files but avoids specific folders such as ProgramData, Recycle Bin, Boot, System Volume Information, and Windows folders.
- After stealing personal information and encrypting the data, it conducts double extortion to get the victims to pay the ransom.
- If the victim refuses to pay the ransom, the stolen data is released on the dark web.
Protective Measures Against Akira
- Maintain basic online hygiene and protection protocols.
- Maintain offline backups of important data and ensure that these backups are up to date.
- Regularly update operating systems and applications.
- Consider ‘virtual patching’ to safeguard legacy systems and networks.
- Use strong password policies and multi-factor authentication.
- Avoid using updates/patches available in any unofficial channel.
With Akira ransomware posing a considerable threat to both Windows and Linux-based systems, adopting preventative measures recommended by CERT-In can significantly mitigate the risk of attacks. As always, maintaining online hygiene and staying updated on system patches is essential in combating such cybersecurity threats.
If you like this post, please share your feedback in the comments section below so that we will upload more posts like this.